
Identity and Access Management (IAM) at the workplace is a comprehensive set of processes, policies, and tools that work together to make sure that the right people gain access to the right systems and data while keeping unauthorised access at bay.
This includes onboarding and identifying each identity, authenticating it with a trusted credential, authorizing access to resources, assigning responsibilities, tracking activities, offboarding, and managing other attributes associated with an individual user.
According to Gartner, “Access management solutions are mature, rich with features and offer a broadened scope that overlaps with many adjacent areas” Gartner further says, “The recent enforced movement to lockdowns and remote work trends has been driving AM acquisitions for tactical emergency response purposes, including securing remote access to employees, workforce and B2B collaboration, and customer portals”
There are five general domains within IAM:
When considering IAM, it’s likely that technology such as two-factor authentication comes to mind. However, industries throughout the global economy are under constant threat of various cyberattacks, and the state of IAM continues to adapt and evolve to stay a few steps ahead of the latest cyber-attacks.
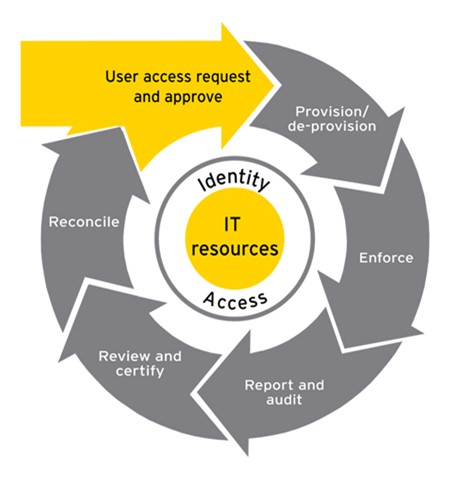
When a new employee starts at a company, IT often provides the employee with access to the corporate network, file servers, email accounts, and printers. Access to these applications is often granted separately by the specific application’s administrator, rather than by a single person in IT. This makes it difficult for the organization to keep track of the access granted.
It’s important to understand who has access to applications and data, where they are accessing it, and what they are doing with it. A lack of visibility results in high risk of security breaches.
Most enterprises have made a significant investment in a corporate directory (such as Microsoft Active Directory) to manage access to on-premises network resources. As organisations adopt cloud-based services, they need to leverage that investment and extend it to the cloud, rather than create a parallel directory and access management infrastructure.
Truly centralising single sign-on and user management requires building integrations with numerous applications and keeping track of the maintenance requirements for new versions of each application. For the vast majority of organisations, having their IT department maintain its own collection of “connectors” across that constantly changing landscape, is unrealistic and inefficient.

To overcome these challenges a strong IAM solution should not only enable IT to automatically add new applications, but it should also provide:
The IAM solution comes with automatic deprovisioning of the access across all systems which makes it more secure and less vulnerable to a breach.
The IAM solution provides deep integration between the AD and LDAP along with other applications which help to monitor security breaches and accesses.
Audit and reporting are important aspects of an organization and so is having a clear audit trail. The IAM solution helps keep track of all the data and accesses by integrating all the silos systems and reducing human intervention to a minimum.
The Access Management solution identifies directory services, single sign-on, strong multi-factor authentication, automated provisioning, automated workflows, and built-in reporting.
It can be used to manage access across all of your applications, providing critical benefits for users, administrators, and executives.
At AMO, we create bespoke Access Management digital solutions tailored to your needs. If you want to know more about our services and how we can streamline your access management processes, get in touch today!
We gather information about your needs and objectives of your apps. Unsure about the app you need? We will carefully assess your top challenges and provide expert guidance on the perfect solution tailored to your success.
We create wireframes and an interactive prototype to visualise the app flow and make changes as per your feedback.
Estimation of the project deliverables including the resources, time, and costs involved.
Showcasing POC to relevant stakeholders illustrating the functionalities and potential of the app to meet business objectives.